Hello everyone,
Today's blog post is a little bit more serious. I didn't think I would release all of this information but unfortunately, I feel a certain urge to do so. It feels like my responsibility to release all of this information, since Curse has not done so or I have not been notified of the problem being resolved. I don't know if this was done on purpose (which would be highly unlikely and I strongly doubt that such a thing is the case for Curse) or that my important emails just didn't arrive, but they have not answered me. They might have been busy, although I am not sure with what, considering the dates of the discovery. For more on those dates, read on.
Summary
The Bukkit.org forums were hacked. Not just a simple hack, but something using XenForo's template system to edit the header template, allowing for script insertion. In short: A script was inserted on every page, sending all form data to a malicious URL whenever the login form was posted. Thousands, maybe tens of thousands (I do not know how frequently these forums are used nor can I tell how long this script was active) of account details were compromised - Many of them could have been accounts with access to whole (Minecraft) servers or databases, in the case of big developers or representatives of big Minecraft networks.
Discovery and details
I discovered this vulnerability on the 11th of November, and I sent curse an email (I contacted them on Twitter, and they gave me an email via private messaging). Here's the email I sent to them:
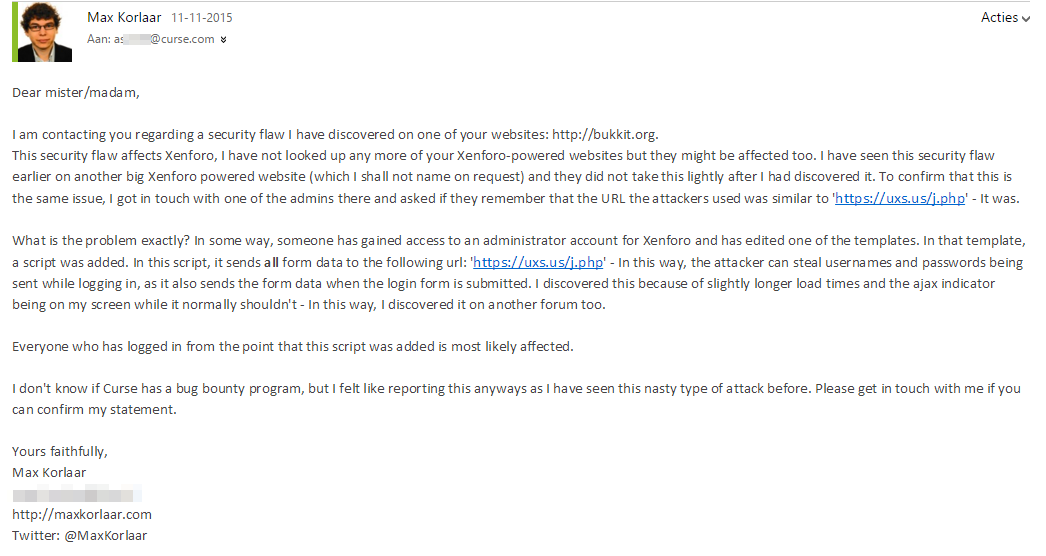
The script that I found actually consisted of two scripts - The one that I have described in the email above, but also a separate script specifically written for the login script. For the curious or technically-minded people out here, you can find a copy of the script here.
The login form was modified; The 'onsubmit'-event was hooked up to the authXen() function. There is proof of the fact that this script was installed on bukkit.org, on the archive.org website. When going back to the 9th of November 2014, you can view the page its source and see that the script is there.
I got into contact with Alex, who replied me with the following:
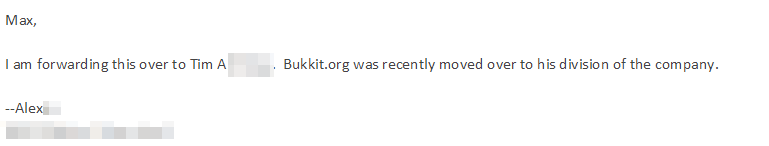
So far, it looked good. My important emails were finally getting through, although it seemed like so.
No response
3 days later, on the 14th of November, I still had not received an answer from Timothy A., to whom I was referred to by Alex. I sent another email, directly addressed to Timothy this time:
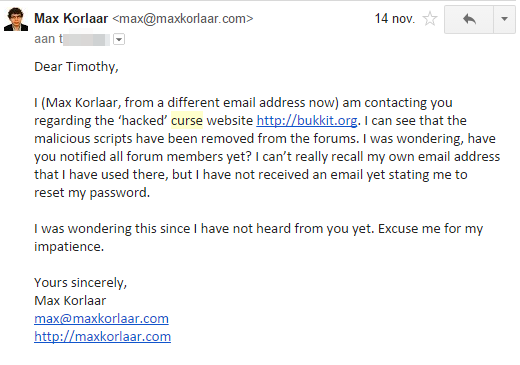 I have had no answer from anyone at Curse to this date.
I have had no answer from anyone at Curse to this date.
This is quite ridiculous. Many people are compromised for sure, including myself. I strongly believe that almost no one is aware of their account being compromised. It is an ethical responsibility to disclose this to your users. It would hurt your reputation if a third party (read: me) would disclose such a hack like this, right?
So, that's why I am writing and publishing this blog post. I've waited for almost a month, and I've not heard anything from Curse. The bukkit.org homepage remains unchanged - The script has been removed, so there is no danger in logging in anymore, but there is no news post. No update, no banner. Have users been notified? I don't know. Probably not, otherwise they would've replied back to me too.
Conclusion
Please get in touch next time, Curse. Next time something as big as this gets discovered, don't just fix it - Set things right. Stay in touch and let everyone know what's up.
Tips and useful practices
- Use different passwords for different services. Do not use a shared password
- Use strong, hard to guess passwords
- Use a service to generate and store your passwords
- Use 2-factor authentication whenever possible
Notes
During the situation, I had trouble using my Gmail account, hence the first screenshot of mine was made in Outlook and the other one in Gmail, however I tried to make sure that it was clear to the recipients that I was both of these senders.
It looks like that I have even been noticed by well-known security researcher Troy Hunt! His popularity even took my website down, combined with some other forum and reddit threads bringing in a lot of traffic.
13th of November 2017: I have edited this post to address some grammatical errors and change some formatting.